📝HMAC
- Hash-based Message Authentication Code
- Can be used to verify both data integrity and authenticity of a message.
- Can be used with any cryptographic hash function.
- size of the HMAC output is the same as that of the hash function
- HMAC does not encode message. The message should be sent along with the HMAC. All other parties will hash the message and should receive the same HMAC value.
- HMAC is not vulnerable to Length extension attack
- inputs:
- key
- message
- output:
- HMAC hash value of fixed length
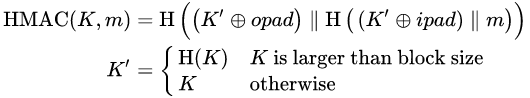
Algorithm:
- two pads are produced from the key (outer and inner) by xoring key with byte-filled arrays of 0x5c and 0x36 respectively.
- these constants are computed so that pads have large hamming distance
- where is concatenation